Adopt zero-trust with PKI-based workforce identities
With a growing hybrid workforce, increasing migration to the cloud, and evolving security operations, adopting zero-trust security is critical.
The zero-trust strategy is rooted in the principle that every user, device, and application should be verified before granting access. As such, strong and verifiable identities are at the crux of implementing a successful zero-trust security model.
IN Groupe's PKI-based identity and access management platform, enables organizations to issue and manage of trusted identities to help mitigate risks, ensure compliance with regulations, and manage authorized access. Trusted identities can be used to securely access facilities and digital resources, sign documents, encrypt e-mail, and more.

Comprehensive, PKI-based identity platform, extendible to all identity-related use-cases
Passwordless login to Windows, cloud applications, and other digital resources
Ready-to-use workflows, automation, self-service
Streamline secure on- and offboarding of all users
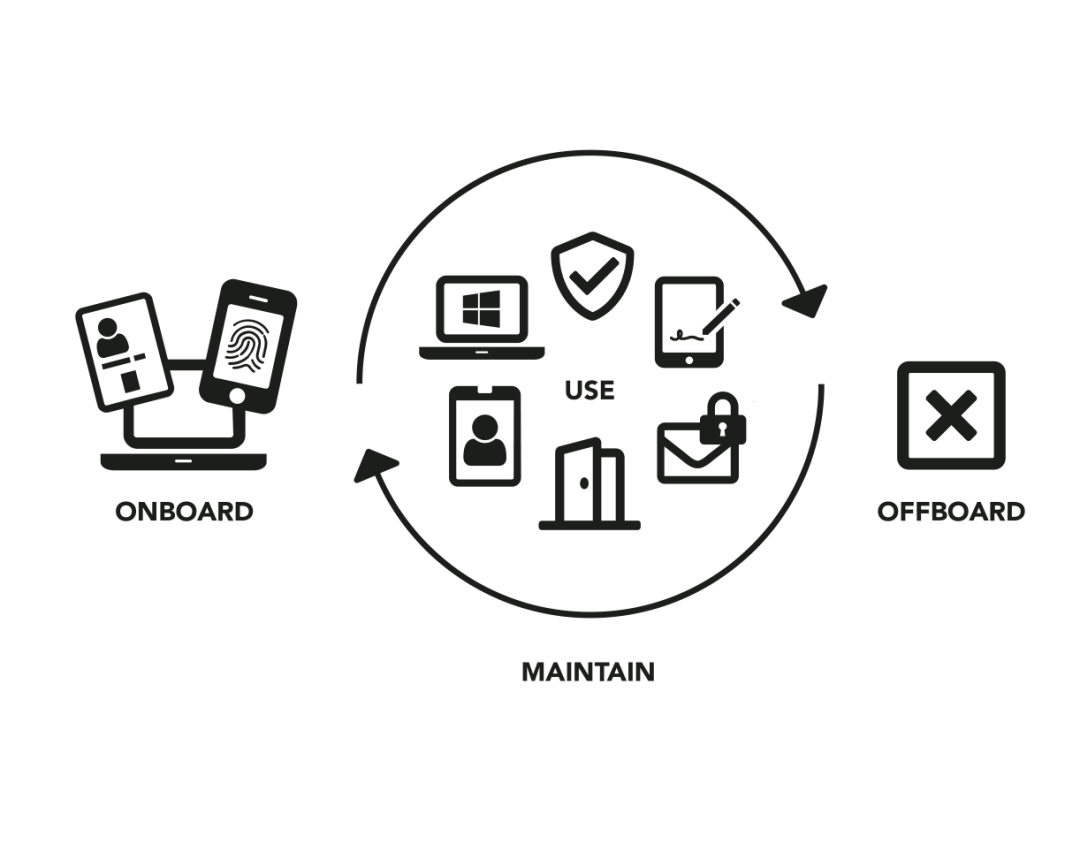
Manage trusted workforce identities
Identities for the workforce are trusted employee identities, most often issued in the form of corporate ID cards or virtual smartcards on phones and laptops.
Employee IDs can be used for physical and digital access, which means that the organization and its employees don’t have to deal with multiple passwords, cards, or tokens.

Manage identities as a service
Managing identities as-a-service offers organizations the convenience of adopting a scalable solution, making it easier than ever to enable digital transformation.
Our service simplifies the lifecycle management of PKI-based identities and credentials through streamlined processes, centralized management, and user self-service.

Best practices for Workforce Identities
Username and password are not secure enough to meet today’s requirements for secure login. Instead, trusted employee identities can be issued in the form of corporate ID cards or virtual smartcards on phones and laptops.
High security
Standards and global regulations compliant solution empowers organizations to secure digitalization and stave off cyberattacks
Comprehensive Solution
Only platform that addresses all use-cases for workforce, workplace, and IoT device identity management
Flexible deployment
The solution can be deployed on-premise, in the cloud, or in hybrid model